Perspectives on Vulnerabilities, ERM, and Audit Services
A fourth Industrial Revolution is underway globally; a digital revolution driven by the rapid, wide-scale deployment of digital technologies, such as in high-speed mobile Internet capabilities, artificial intelligence (AI), and machine learning. Cloud computing is at the vanguard of this transformation. As a result, organizations of all sizes, sectors, and geographies have substantially and rapidly increased their use of cloud computing. According to Gartner (2019), more than one-third of organizations see cloud investments as a top-three priority. The public cloud services market is projected to reach a staggering $266 billion in 2020.
One driver in this proliferation and widespread use of cloud computing is the current digital transformation. In a 2016 address, Microsoft CEO Satya Nadella advanced this enduring description of digital transformation: “becoming more engaged with their customers, empowering their employees, optimizing how they run their business operations and transforming the products and services they offer using digital content.” Such benefits from a cloud computing perspective include managing and outsourcing costly and difficult-to-update and -manage in-house IT infrastructure; streamlining and scaling storage, software, and application support; increasing speed and processing; reducing costs. As a result, organizations of all sizes, geographies and sectors, including CPA firms and their clients, are developing their own private cloud or purchasing public cloud services from cloud service providers (CSP), such as Microsoft Azure and Amazon AWS.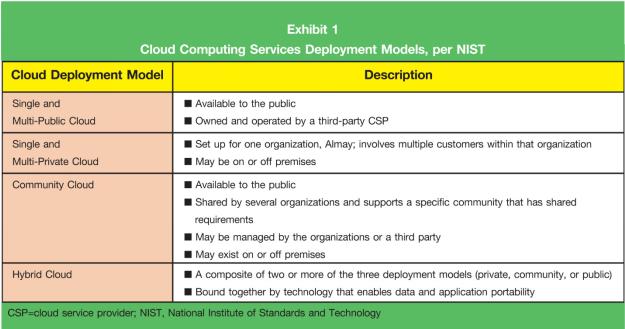
While such potential benefits are compelling, market intelligence reveals that cloud computing exacerbates risks and creates new and unexpected risks. For example, a cloud security breach exposed the names, addresses, and account details of as many as 14 million U.S.-based Verizon customers. In this context, one can only imagine the potential cloud-related cybersecurity breaches and service failures that may emerge from the unexpected disruption and rapid transformation to remote working caused by the current coronavirus (COVID-19) pandemic. On the one hand, workers unexpectedly transitioning to remote working have been enabled in part by cloud computing to immediately, rapidly, and seamlessly access necessary data, software, and applications. On the other hand, such an unanticipated disruption and rapid transformation has exacerbated existing risks and created new risks as workers access data from remote locations; for example, breaches in data confidentiality, unauthorized access, and system availability failures.
The Cloud’s Impact
The National Institute of Standards and Technology (NIST) defines cloud computing as a means for enabling on-demand access to shared pools of configurable computing resources (e.g., networks, servers, storage applications, services) that can be rapidly provisioned and released. In simple terms, the cloud is a massive cluster of super-sized servers housed in locations scattered around the globe (i.e., cloud farms). Cloud farms are operated by CSP vendors such as Amazon AWS; these vendors provide a range of hosting services.
Exhibit 2
Cloud transparency.
The KPMG Audit Committee Institute highlighted “understanding technology’s impact”—with a reference to cloud computing—as one of their seven items to consider for the audit committee’s 2020 agenda. In this context, an organization needs transparency into the nature, scope, and location of CSP vendors and the performance of their cloud activities. The board, senior management, and CPAs should ask the following questions:
· What is our enterprise-wide cloud footprint?
o Do we have an inventory of cloud activities?
o Where are our servers, software, and applications?
· Who is responsible and accountable for cybersecurity, system recovery, and controls?
o Is there a heat-map valuing data stored in private and public clouds, by location?
o Are shared-responsibilities for performance, availability, cybersecurity, and third-party assurance clearly defined and formalized in a service level agreement (SLA)?
o Which global jurisdiction regulations are we subject to?
o Do management, the board, CSPs, and auditors understand cloud risks?
o What are the CSP contractual requirements and SLA terms and commitments?
· Who is accessing our data, and why? Can they see our draft 10-K and trade secrets?
o Do our primary CSPs subcontract our cloud needs to other CSP subcontractors (i.e., third- and fourth-party risk)?
o Are other jurisdictions accessing our data and surveilling our activities?
o Do accountants, lawyers, and other vendors safeguard access and storage of our data?
· Is shared responsibility for risk management strategy, methods, and skills designed properly and operating effectively?
o Are we monitoring breaches and system failures on a continuous basis?
o Are stakeholders effective and accountable to those who share responsibility for governance?
o Are we conducting a top-down enterprise risk management assessment?
Adapting to Digital Transformation
The emergence of cloud computing and the incipient digital transformation of business is having a profound impact on the traditional techniques and services provided by CPA firms. Organizations adopting or leveraging cloud computing should obtain a continuous update of their inventory of cloud activities, including the nature, scope, and locations of their cloud activities; conduct a holistic, enterprise-wide, what-can-go-wrong analysis, including cybersecurity risks and single-point-of-failure risks associated with their cloud ecosystem; and perform an analysis of cloud computing resiliency, including an ERM analysis of cloud performance, security risk, and change management risk. CPA firms adapting to digital disruption and transformation must obtain an understanding of the implications of cloud computing on their clients’ business and control environment; analyze risks of material misstatement and cybersecurity risks; assess cloud controls; and manage cloud-informed changes to the CPA firm’s QC processes and compliance.